There's hardly anyone who doesn't get annoyed with the "create a stronger password" pop-up message when setting up a new account or email. Especially when they’ve come up with an easily remembered mix of words and numbers.
But the businesses that programmed their software to ensure strong password security don’t do it to irritate their clients — they do it to protect the data shared across the accounts. This article explains how to safeguard corporate accounts and prevent possible damage by enhancing password safety.
Why is password security important?
In the digital realm, a password is like a key to your house — if someone gets it, you can kiss your valuable things goodbye. And since data is what the online world values the most, passwords become targets for data hunters. Your task is to minimize the risk of having your employee’s credentials stolen or hacked for the following reasons:
- To prevent identity theft and blackmailing
- To avoid charges and lawsuits
- To eliminate the risk of system breakdown
- To make data breaches less likely
- To ensure continuity of processes
According to the 2021 Data Breach Investigation Report, 61% of investigated breaches involved issues with credentials. 25% of the reported breach cases happened as the result of stealing creds. According to IBM, credential hacks cost 537 businesses over $4.37 million. These stats prove that password hacking happens often and costs dear. But you can prevent it by implementing password policy best practices we’ll explore below.
How does a password get hacked?
Bad actors can hack passwords and get access to your clients' or employees' accounts or profiles in several ways. For example:
- Phishing and social engineering. These techniques try to make users do something they shouldn’t. Methods differ. For example, you’ve probably seen a friend posting about their account being hacked and asking you not to respond to any texts and emails coming from the pretender. Or you might have received a bogus email claiming that your bank asks you to verify your account details. Scammers can even call you and ask to log in to your account on your behalf.
- Blackmailing. Hackers may simply send texts and demand giving the creds. Otherwise, they threaten to do something the users wouldn’t like: post their private photos, leak data, or send some incriminating files to the police. In most cases, this is pure bluffing, but people may panic, and such emails/texts can push them to provide passwords voluntarily.
- Malware. From code that makes your phone freeze to keylogging — there are plenty of programs that can be secretly installed on the device after you download a fishy program or click on the link. Keylogging is particularly dangerous. There is no such thing as unhackable passwords for this technique because it records whatever you type in the sign-up or log-in fields.
- Brute forcing. Brute forcing means guessing the passwords without any context or clues by trying every possible character combination. This technique often includes credential stuffing when scammers use stolen username and password pairs to gain access to the system. And it makes sense: 51% of people use the same password for several accounts, doing hackers a huge favor.
- Guesswork. There are also cases when hackers know a bit about a user and use this knowledge to generate random passwords. For example, some people don’t want to bother creating complicated passwords, so a combination of their names, important dates, or even the good-old ‘qwerty1234’ or ‘1234567890’ might open the door.
The bad news is that these aren’t the only ways hackers can mess with the passwords. They invent new tactics and strategies all the time as soon as people crack their old tricks. The good news is that some common signs can warn you that there’s something wrong going on with the accounts. So, how to check if the creds are in danger?
How to know your credentials were compromised
Password security audits are the best way to check if someone’s hacked your employees' credentials or if they are too easy for scammers to guess. Password audit software runs across the system and, similarly to malware, tries to guess the passwords to assess their safety. It shows which accounts use potentially hackable passwords and which ones are OK for now.
However, auditing software isn’t the only possible solution to check if your employees’ passwords are at risk. Here’s the list of other typical signs.
- Your employees’ accounts show suspicious activities. If your employees notice concurrent sessions linked with another device, browser, region, or country, it means that someone has logged in by using stolen creds. Any suspicious activities involving their accounts—payments, withdrawals, or unauthorized transfers—are a sure-fire sign that a hacker got access to the accounts.
- Your software vendors suffered a data breach. If this happens, all company's accounts associated with this vendor are compromised. In this case, you should report to a cybersecurity agency, change passwords, and start an emergency backup.
- Your employees receive emails about unsuccessful log-ins. Some companies limit log-in attempts, and after three or four tries, they send an email to the user to verify it was them. If your employees get these messages but haven't logged in recently, someone else is trying to do it.
- Their accounts are on the “hacked” list. There are databases with the accounts and emails involved in data breaches. Your employees can check if theirs are on the lists, and if they are, it means that their passwords were hacked. In this case, they need to change passwords and run a device/network check for malware.
If your employees notice any of these red flags, they should immediately terminate all sessions, contact a cybersecurity agency, change passwords, and audit the systems for security. Done timely, these strategies will help you avoid data leaks and system breakdown.
Now you know how hackers can get the passwords and what signals about their success. It’s time to make their lives harder by using password protection strategies.
Protecting passwords: Standards and best practices
Even if your IT team is the best, weak passwords set by your staff can take down the whole system. Here's how to create a strong password culture and make sure that your employees follow its principles.
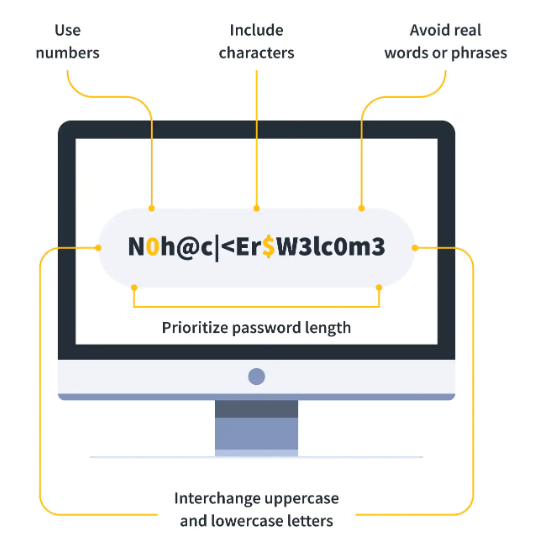
- Enforce stronger passwords. Invest into code that automatically checks the password complexity. Without a strong enough password, your employees/clients won’t even be able to create an account.
- Enable two-factor verification. Authenticate each session with two-factor verification procedures. Each time a user wants to log in, verify it’s really them by using automatically generated codes. Avoid sending text messages since they can be tracked and used by hackers, too. Instead, use call-based authentication tools, where your clients need to type in the last digits of the incoming phone call number or listen for the code supplied by the caller. We wouldn’t recommend using password security questions as a second authentication layer, either. People tend to use the same ones for different accounts, so they can be easily hacked.
- Encourage using backup emails. In case the password was hacked, and the scammers changed it, backup emails will help employees recover their passwords.
- Activate unique password checkers. These tools check new passwords against the previous ones for accounts across specific platforms or solutions. When enabled, these checkers won’t allow the employees to reuse the passwords.
- Change passwords only when needed. Despite some tools asking users to change passwords every X days, this strategy isn’t a good one. First, it doesn’t enhance security. Second, the more often the users change passwords, the more likely they will use simpler, more memorable ones. Ask your employees to change passwords only when they notice suspicious activity with their accounts.
- Use password manager tools. If an employee needs access to various systems or accounts, they will have to use a range of passwords. Don’t compromise security and get their memory overburdened—use password manager tools in your environment. LastPass, 1Password, Google Password Manager, or similar apps will require a master password or biometrics to log in. They can also generate strong, hard-to-hack passwords.
These are the most common techniques to secure your corporate account passwords. Now let’s move to the to-avoid list.
Worst password safety strategies
Some employees might be afraid that complicated passwords will send their memory into overdrive. So they store passwords on sticker notes or go for combinations that are easier to remember. They might even share their creds with colleagues when they need their help with assignments. All that compromises password security and system safety, so strongly advise your employees against such practices. Let’s explore these and other poor password security practices in more detail:
- Keeping the password too short and simple. It’s a bad practice to use only letters or only symbols or digits in passwords, all in the same case. It narrows down the number of combinations, and a password becomes too weak. Having a year that marks the end of the Jin dynasty for a password is also a bad idea because it’s 1234. Instruct your employees to keep their passwords between 8-12 characters, mix and match numbers, digits, and symbols, and avoid dictionary words. For example, Morgan12_chase67 is still a weak password compared to Ygs9-1q,PsG’szRRtA.
- Keeping it too obvious. ‘qwerty123’, ‘1111111111’, ‘batman0987654321’ or passwords that include user’s personal information or dictionary words are too obvious—and too easy to hack.
- Using previously used passwords. It might save the memory resources, but it’s a road to making the hacker's job easier in the long run. These passwords may already be on the hacked list, so your employees might involuntarily open other accounts to scammers.
- Using the same password for multiple accounts. This is another failing strategy to avoid as it endangers several accounts at the same time. Plus, it makes emergency password recovery impossible if your recovery email has the same password as your compromised one.
- Storing them in public. By ‘public,’ we mean any digital or physical place where people can save their passwords (digital notes, paper notebooks, stickers, saved messages, etc.) They are easily accessible, and stealing them would be no feat.
- Sharing passwords. Ideally, this should be penalized as it can go against the NDA signed by the employees. You should develop a strong policy against password sharing to prevent data leaks and potential breaches.
- Using obvious hints. This will make the guesswork a piece of cake. When setting up hint or security questions, instruct your employees to use the information only they know.
- Logging into accounts using unsecured networks or devices. Accessing corporate accounts via an unprotected network exposes the data to hackers snooping around.
Now let’s imagine that you did your best to enforce password safety. But passwords to your corporate accounts got hacked anyway. This is what you can do to mitigate the consequences.
What to do if the passwords have been hacked?
If your employees realize something’s off with their accounts, here’s a five-step plan how to reduce the damage.
- Ask your employees to change passwords immediately to lock the accounts. If it’s impossible for some reason, have them start emergency password recovery.
- Contact your IT team and ask to run diagnostics on all devices and systems. This will help detect what accounts and software have been compromised.
- Contact cybersecurity agency. A data breach doesn’t look good for the company’s reputation, so go the extra mile to keep your client’s data safe.
- Prepare to launch an emergency backup. Hackers might delete data from the source platforms and accounts. Be ready to launch emergency recovery to copy the data.
- Freeze any assets associated with the affected passwords and emails. If it’s the financial account’s password that got hacked, contact your bank and ask to freeze any activity with the funds.
Make sure to update all your software to the latest version and change the passwords after finishing recovery and backup.
Make your password secure again!
Password security is the first step to keeping your whole ecosystem hacking-proof. Cultivate safe password policies in your business to help your employees protect their accounts and data from cyberattacks—and avoid corporate damage. Make sure that your team uses password managers, creates strong passwords, and keeps them private. And if anything goes south — you have a plan to mitigate the consequences fast.
Data backups made simple
Automated. Secure. Fast.



